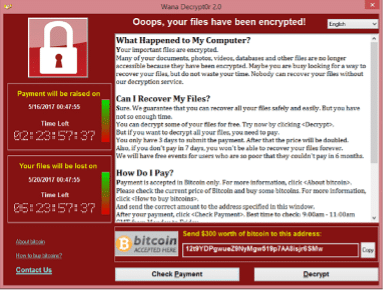
It’s one of the most frightening messages you will ever receive in business. It’s even designed to look frightening, and it tells you that all your critical data assets have been either encrypted or stolen, and you must pay a hefty ransom to get them back. Your stomach drops and your skin goes cold.
You probably experience a mixture of feelings, including anger, frustration, fear, and violation. You’re especially frustrated because you know it began when someone in your company made a mistake. Read on to learn more about cloud PCs for ransomware recovery and how they help with risk mitigation.
How Vulnerable Are You to Ransomware?
An overwhelming number of experts cite phishing attacks and ransomware as the most common kind of cyberattacks happening today.
- The FBI Internet Crime Complaint Center (IC3) reports receiving 791,790 complaints from the American public in 2020 totaling over $4.1 Billion in losses, a new record.
- A chilling report from CyberCrime Magazine estimates that global ransomware damage were $20 Billion by 2021 with a new attack occurring every 11 seconds. Their estimate is that it will reach $265 Billion by 2031 with a new attack every 2 seconds.
In their Cybersecurity Framework Profile for Ransomware Risk Management, the National Institute of Standards and Technology (NIST) defines ransomware as, “A type of malicious attack where attackers encrypt an organization’s data and demand payment to restore access.”
According to NIST, ransomware attacks begin with the arrival of a phishing email, defined as, “A digital form of social engineering that uses authentic-looking—but bogus—e-mails to request information from users or direct them to a fake Web site that requests information.”
One of your end users receives a “phishing” email, opens it, sees it as authentic, and follows the instructions to either click a link or open an attachment.
When they do, the doors get thrown wide open. The attacker now has full access to everything that user has, and maybe even more. They can exfiltrate the data, stealing it, or they can simply encrypt it. Without the attacker’s key, the organization’s data instantly becomes useless to them, unless they pay the ransom, which last year ranged as high as $40 million from one large insurance company. They pay because the operational downtime caused by such an attack lasts three weeks on average and they simply cannot afford it. How much will a ransomware attack cost you?
Number One Risk? An End User Clicking a Link
Unfortunately, your end users are the weakest link. You can scan every incoming email for inconsistencies and anomalies, but some will still get through looking authentic enough to deceive the unsuspecting.
Once a phishing email makes it through IT’s defenses, you are completely dependent upon the training you’ve provided to your end users to protect the organization from what will happen if they click that link. Unfortunately, the cybercriminals are that good at it. Even the most observant, conscientious user may be fooled. It’s truly unavoidable.
Yes, Covid Made Security Risks Worse
Literally all data and network security systems were severely challenged when everyone left offices to work from home during the Covid-19 pandemic. The reason has everything to do with your threat surface, the network area you need to protect, scan, and hunt for threats in.
When your entire network and company were in one building, your threat surface was in and around that building. If you had more than one location, you had more than one threat surface. You adjusted your protection accordingly.
How many users did you send home to work? That’s how many threat surfaces were spawned at the start of the pandemic, and in many cases remain today. If your network connects to a location, that location becomes part of your threat surface, and you must protect it. With home users, that was made worse by the fact that they were using residential-grade internet access, hardly the level of infrastructure you want to have to protect.
Circle the Wagons For Greater Protection
We all want the pandemic to be over, and some of us will return to our offices when that happens. Many may continue working from where they are. It looks like hybrid workstyles are here to stay, and that means people will continue working all over the globe. That means your threat surface remains too large to manage yourself. Since IT can’t control end user behavior, a different approach is needed.
With everyone working everywhere, how can you dramatically reduce your threat surface back to something very manageable? What if you didn’t have to worry as much, and desktop security, reliability and availability was actually managed for you? Here’s what you need to know about cloud PCs for ransomware recovery.
Workspot SaaS cloud PCs: Designed for enhancing security, resilience, and rapid recovery in a ransomware-plagued world
The Workspot Enterprise Desktop Cloud™ is a SaaS platform for delivering cloud PCs. With Workspot, all your desktops are running in one of the dozens of Google Cloud and Microsoft Azure data centers located around the world. These major cloud providers invest billions of dollars in data and network security, far more than any single enterprise could spend, so you immediately enjoy all those security benefits that you otherwise could not achieve. That cloud data center becomes your threat surface, and it’s among the best protected threat surfaces anywhere.
Each of your users connects to a Workspot cloud PC from their laptop, smartphone, desktop computer, Chromebook, or any other device of their choosing. It’s just an access session running on the end user’s physical device. That’s all that’s running on that device. Everything else runs in the cloud data center on Workspot’s SaaS cloud PC platform. Attackers can still attack those users’ physical endpoints, but they’ll be wasting their time. All they’ll get to is an application that does them no good at all. Try to go further and they face powerful cloud provider security as well as Zero-Trust protection monitored 24/7 by Workspot. They’re not getting near your data because it is all located remotely in the data center.
The difficult reality is that no single solution can prevent ransomware. Today, security software is table stakes. Continuous monitoring solutions that assist with prediction and prevention in addition to reaction are the modern approach.
Most proactive monitoring methods focus on what happens inside the desktop operating system or on anomalous traffic traversing the internal network. Workspot Watch™, an innovative big data collection and correlation engine, in conjunction with our Network Operations Center, adds an additional layer of 24×7, real-time oversight of your entire cloud PC implementation globally. By collecting and correlating millions of data points across every cloud PC, within every cloud region, and across multiple clouds, it monitors for anomalous, troublesome patterns. Once spotted, the Workspot support and customer IT teams are alerted – in real time, possibly before anyone else identifies a brewing problem – so incident teams can communicate the issue and take immediate action to limit the damage. This capability gives Workspot customers a multi-layered defensive line and alert system that includes cloud provider security measures, Workspot Zero Trust enforcement, and the customer’s SIEM system.
As soon as ransomware activity is detected or reported, the reaction solution focuses on the restoration of your most recent full backup. Since cloud PCs can be configured to create backups once every day, your maximum recovery point objective (RPO) – the maximum amount of data that can be lost after recovery – is one day. You may also establish a second recovery point, perhaps two days or a week or a month ago. If somehow the cybercriminals managed to damage your daily backup, you still have a viable backup to restore. Because the data, the backup, and all your users’ PCs are located in the cloud, failover is instantaneous, your RPO is minimized, and your recovery time is quick; your users can be back up and running in as little as five minutes.
Five minutes to recovery when you have Workspot cloud PCs.
Is that rapid enough?
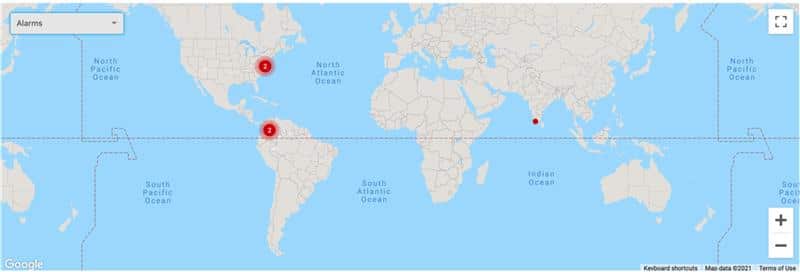
The Workspot Network Operations Center generates alarms highlighting areas of concern
so potential issues can be addressed quickly.
More cloud PC security benefits – keeping up with the patches
What happens today when you hear the word “patch” or “update” in a distributed, work-from-home world? Feel your blood-pressure rising? How do you patch computers not on your network?
You probably conjure images of technicians all over the place interrupting everyone’s day to sit down and apply those patches and updates in every location you manage. You shudder at the likely error rates and delays you’re going to create.
With Workspot, that just doesn’t happen anymore. All desktops are centralized and always reachable by IT and IT’s existing tools. There’s no need to track your end users down to implement critical updates! All patches and all updates are applied in the data center without any intervention by your end users or field technicians. Workspot delivers cloud PCs to all your users and maintains all of them for you. No end user involvement. No end user errors. Read more about all of the innovation that drives Workspot’s unique ability to secure your cloud PCs.
The Workspot Cloud PC Defense Against Ransomware
Here’s a simple checklist of what you can do right now to defend against security breaches and ransomware with Workspot cloud PCs for ransomware recovery on Google Cloud and Microsoft Azure:
- Leverage Azure and Google Cloud and the deep investments they make in data and network security
- Move your desktop workloads to those public clouds
- Reduce your threat surface from potentially thousands of locations to just a few regional cloud data centers
- You bring your Windows image, your multi-factor authentication (MFA) preferences, your existing management tools and more and Workspot delivers secure cloud PCs that just work to all your end users
- IT teams manage their cloud PCs just as they would manage physical PCs; no training required!
- Enhance your security posture via Workspot’s Zero Trust Security architecture innovation
- Improve your ability to predict a brewing security problem via Workspot Watch 24×7 monitoring
- In the event of a user being trapped by ransomware, your return to full function is about five minutes
- Avoid paying a ransom!
If that all sounds like the calming relief from security and ransomware worries you’ve been seeking, schedule a demo with us so we can show you how it works!